
The pro-Russia hacker group NoName057(16) reportedly claimed it was behind Denial of Service (DoS) attacks against the Finnish parliament’s website on Tuesday, the day the country joined NATO. The country’s Technical Research Centre of Finland was also hacked, according to Finnish news site, YLE. NoName057(16) is the same group that took responsibility for a distributed denial of service attack, taking down the website for the country’s parliament last August, and who also attacked Ukraine, the U.S., Poland and other European countries.
In January, multiple outlets reported that GitHub had disabled NoName057(16)’s account after the group was linked to attempts to hack the Czech presidential election candidates’ websites.
Jump to:
- Israel hit by Killnet proxy
- Killnet drives big increase in attacks worldwide
- With DDoS attacks rising, defense depends on security providers
Israel hit by Killnet proxy
This week, Russia-aligned hacktivists also attacked one of the biggest names in security, Check Point, along with universities and medical centers in Israel, the Jerusalem Post reported.
The group called itself “Anonymous Sudan,” but Nadir Izrael, CTO and co-founder of asset visibility and security firm Armis, said the attacker is likely aligned with pro-Russia hacktivist group Killnet.
“For the most part the way security companies track these groups is based on the kinds of messages they post and similarities in text and tools,” he said. “The messages that come from these groups are mostly in Russian and English. It’s a bit like how the FBI does profiling: they look for similar MOs and tools, and backtrack to sources. In the case of DDoS attacks you are looking at lots of different devices worldwide from different regions of the world that are all at once trying to access a certain web site.”
He noted that the threat actor itself had said it would next attack on Friday, April 7, 2023, as part of the annual OpIsrael, when hackers and hacktivists attack Israeli organizations, companies and personalities.
“Even if the disruption itself doesn’t seem prominent, a cyberattack on a government or an organization can create an underlying fear of chaos amongst citizens,” he said, adding that 33% of global organizations are not taking the threat of cyberwarfare seriously or were “indifferent.”
Killnet drives big increase in attacks worldwide
Killnet ramped up attacks against U.S. entities this year and last, according to application performance management firm NetScout. In a new study, Unveiling the New Threat Landscape, NetScout said that the U.S. national security sector experienced a 16,815% increase in DDoS attacks in the second half of 2022, many related to Killnet. These included a spike in attacks after President Joe Biden’s public remarks at the G7 Summit in June 2022, and another spike the day Biden and French President Emmanuel Macron announced their continued support of Ukraine in December 2022.
The average cost of cyberattacks to health care systems in the U.S. between March 2021 and March 2022 was $10 million. Last year, the average data breach cost worldwide was $4.35 million, Statista reported.
NetScout’s ATLAS sensor network, which it says covers over 400 terabytes per second of international transit, collects DDoS attack statistics from an average of 93 countries daily. This encompasses over 50% of the world’s internet traffic, according to the company. In its report, the company said the peak sum of DDoS alert traffic in one day reached 436 petabits and more than 75 trillion packets, in the second half of 2022.
The firm said exploits against websites by Killnet and other groups in the last six months of 2022 drove much of the 487% increase in HTTP/HTTPS application-layer DDoS attacks since 2019. This kind of attack hobbles web servers and protocols that enable networks to communicate, making it impossible for a site to deliver content (Figure A).
Figure A
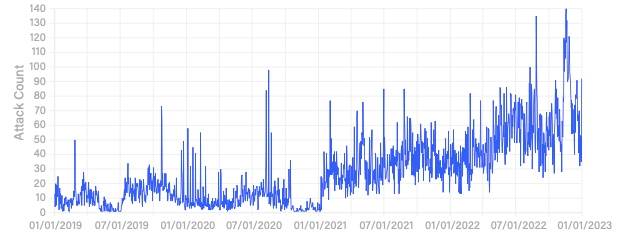
“DDoS attacks threaten organizations worldwide and challenge their ability to deliver critical services,” said Richard Hummel, threat intelligence lead of NetScout, in a statement. “With multi-terabit-per-second attacks now commonplace, and bad actors’ arsenals continuing to grow in sophistication and complexity, organizations need a strategy that can quickly adapt to the dynamic nature of the DDoS threat landscape.”
The company said direct-path attacks and traditional reflection/amplification attacks have increased by 18% over the past three years.
NetScout also found that:
- In 2022 some 1.35 million bots generated by such malware as Mirai, Meris and Dvinis drove some 350,000 security-related alerts, 60,000 of them issued by service providers.
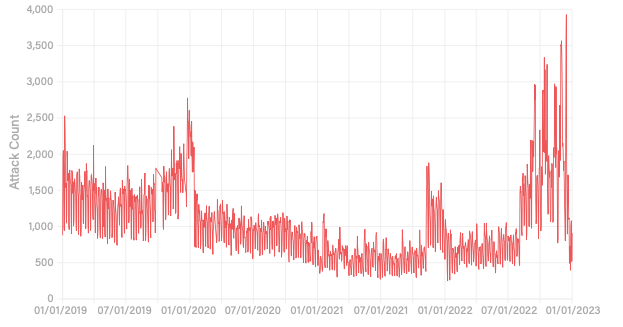
- Carpet-bombing attacks, a technique that simultaneously targets entire IP address ranges, increased by 110% from the first to the second half of 2022, with most attacks against internet service provider networks (Figure B).
Figure B
Europe, the Middle East and Africa’s optical instrument and lens manufacturing sector experienced a 14,137% increase in DDoS attacks, mainly against one major distributor with more than 6,000 attacks over the course of four months.
The telecommunications industry has experienced a 79% growth in DDoS attacks since 2020 because of the rollout of 5G networks to the home.
NetScout’s research also found that DNS query flood attacks have more than tripled since 2019, a 243% increase in adoption of this attack technique. The average daily attack count for 2022 is approximately 850 attacks, a 67% increase from 2021.
According to NetScout, these attacks targeted national security and commercial banking sectors in North America, Europe, the Middle East and Africa (Figure C).
Figure C
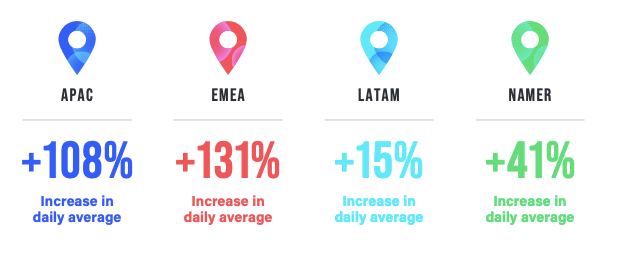
“There is a high degree of certainty that these attacks are almost exclusively related to the ongoing conflict between Russia and Ukraine,” the firm said.
With DDoS attacks rising, defense depends on security providers
There is no easy fix for DDoS attacks because they can exploit numerous vulnerabilities. DDoS protection service providers might be needed for larger, more complex organizations. Depending on the volume of attacks, firewall solutions may also suffice.
Defensive measures include taking such actions as identifying and patching operating system and application-level vulnerabilities, closing ports, removing system access and putting servers behind a proxy or a content delivery network. Specialized training in ethical hacking and other defensive measures is invaluable, especially given the shortfall in cybersecurity talent.
To gain cybersecurity skills and certification for your enterprise, learn about the TechRepublic Academy Advanced CyberSecurity Professional Certification Bundle here.







