
- What is advanced threat protection?
- What does advanced threat protection do?
- How to choose advanced threat protection software
- Best advanced threat protection software
Just as malicious actors refined virus, phishing and ransomware attack practices and technologies, so have cybersecurity providers improved corresponding defenses. By leveraging artificial intelligence and machine learning within endpoint protection and cyber-defense solutions, advanced threat protection software learns from and automatically applies newly learned information to better identify, resist and arrest cyberattacks.
What is advanced threat protection?
Advanced threat protection refers to dynamic endpoint protection and cyber defense solutions that use both AI and ML technologies to better recognize and defend against skilled phishing efforts, sophisticated ransomware threats and other particularly advanced cyberattacks.
What does advanced threat protection do?
In the past, endpoint protection software frequently compared file signatures against known threats, taking action when matches occurred. The problem with that strategy was older cybersecurity software couldn’t adapt to changing conditions, learn from mistakes or intuitively determine when new behaviors proved risky.
SEE: Mobile device security policy (TechRepublic Premium)
By incorporating and enabling AI (technology that assists computers in thinking like humans and imitating human response) and ML (itself an AI technology that assists computers and applications from learning from past events) advanced threat protection more effectively detects and resists both old and new threats, including new exploits as they appear and evolve, that use advanced techniques to try to steal or corrupt sensitive information. Whether incorporated within endpoint protection agents or assisting in the form of a hardware appliance or email or firewall filter, advanced threat protection technologies assist network administrators by providing tools and technologies that continuously monitor for threats, mitigate attacks before they occur, disrupt in-progress infections and even suspend active attacks.
How to choose advanced threat protection software
Organizations should select an ATP solution that provides the coverage and functionality the firm’s security requirements demand, while also ensuring the chosen offering demonstrates reputable results and matches the company’s budget. Firms should pay particular attention to features and functionality, as some organizations may place greater emphasis on ease of use, while others may value advanced reporting capabilities and broader application (on-premises software programs as well as cloud-based protection, including for a variety of platforms, including databases, CRM and ERP platforms, Active Directory domain and identity administration and email) instead.
Best advanced threat protection software
A variety of providers offer advanced threat protection software. Here’s a look at leading solutions.
Check Point Harmony Endpoint Protection
Check Point, a long-prominent security software and hardware provider, integrates many advanced threat protections within its Harmony Endpoint Protection services. With a half-dozen different Harmony Endpoint packages, the cybersecurity solution is designed for a wide range of organizations, including small and medium businesses, and uses both Harmony cloud-based services and an on-premises appliance to power operations.
With next-generation antivirus, broad compatibility with Windows, macOS and Linux, and management either on-premises or using a cloud service, the platform provides phishing, ransomware, common exploit, credential, behavioral, email and URL protections. Built on Check Point’s Infinity consolidated security architecture permitting service and safeguard expansion for sites, endpoints, devices, networks and cloud platforms, the solution automates the majority (the firm claims 90%) of attack detection, investigation and remediation events.
Pricing is per endpoint per year, with individual components beginning at $4 per user per month.
Check Point Quantum Network Security and SandBlast Advanced Network Threat Prevention
Targeting enterprise organizations, Check Point’s SandBlast Advanced Network Threat Prevention provides protection against zero-day and other common threat vectors. Wrapped within the company’s Quantum line of network-protective security solutions, the offering melds SandBlast threat prevention with Check Point’s expansive and highly scalable Quantum network security capabilities.
In addition to a centralized management platform, Quantum network security services offer data center-grade performance, a variety of appliances and ferocious performance up to 1.5 terabit per second security services throughput, although scaled solutions are also available for individual branch offices. Built on Check Point’s Infinity architecture, Quantum solutions include next generation firewall services, the SandBlast threat emulation and threat extraction features, antivirus, identity protection, app controls, anti-spam technologies, anti-bot and URL filtering, among other features.
Pricing varies widely depending upon the specific solutions, appliances, configurations and options.
CrowdStrike Falcon Prevent
With a broad array of offerings, CrowdStrike presents an ATP approach with its AI-powered Falcon line of security solutions. Falcon Prevent is the foundational advanced threat endpoint protection service CrowdStrike offers businesses of all sizes.
Falcon Prevent is the next-generation antivirus solution that uses AI and ML to detect and defend against a range of known and emerging threats. With automated indicators of attack remediation, in which Falcon software works to not only detect suspicious attack behaviors but also the intent of those actions, the platform also works to remove detritus left behind when malicious events are disrupted and arrested.
The solution boasts a variety of features and functions. From simple deployment and administration to full-fledged reporting, an example of which is shown in Figure A, the product also features a lightweight install that doesn’t slow systems or user productivity.
Figure A
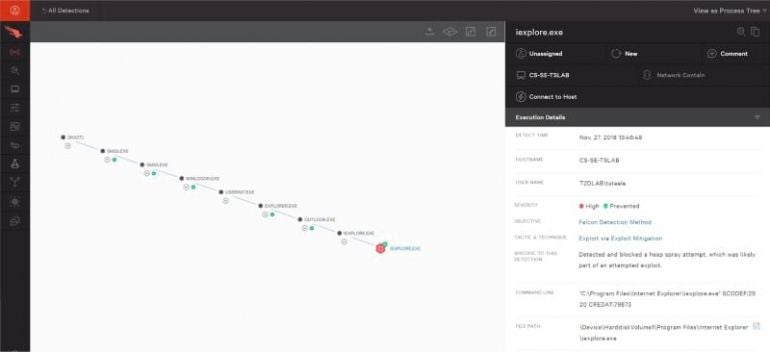
Compatible with Windows, macOS and Linux, CrowdStrike Falcon Prevent works without requiring on-premises equipment. Free trials are available. Pricing starts at $59.99 per endpoint per year.
Darktrace for Endpoint
With a self-learning AI-powered engine, Darktrace for Endpoint provides organizations of all sizes with cyberdefensive software that seeks new and unique threats while also safeguarding against advanced attacks. With automated threat investigation and its Autonomous Response, the platform protects against a range of vulnerabilities, from zero-day threats to unusual or malicious user activity.
Capable of protecting remote workers, cloud solutions, email and multiple sites and networks using its proprietary cSensor agents, the platform can neutralize many threats in just seconds. Human interaction need not even occur, thanks to the platforms automated response behaviors.
List pricing for the detection and response product begins at $10 per device per month. Darktrace for Endpoint can be deployed as a standalone software-only product but is usually deployed in combination with Darktrace for Email and Darktrace for SaaS in order to provide comprehensive device, computer and user account protection. Licenses are available from resellers, as well as Darktrace itself and the Amazon Web Services marketplace.
For more information, call Darktrace at 1-415-229-9100.
FireEye Endpoint Security
Claiming its solution prevents the majority of endpoint cyberattacks, FireEye Endpoint Security adopts a strategy, highlighted within Figure B, in which the antimalware program combines a signature-based endpoint protection engine with AI and ML technologies to better detect and block threats. Deployable onsite or via the cloud, the endpoint security solution adds key AI and ML features to surface advanced threats.
Figure B

FireEye’s MalwareGuard includes machine learning capabilities that benefit from additional data gained battling previous cyberattacks and breaches. ExploitGuard, meanwhile, applies behavioral analysis tools to determine whether exploits are being attempted and, subsequently, stopping them from succeeding. Yet an additional tool, ProcessGuard, defends against credential exploitation.
A component of FireEye’s broader XDR platform, which connects a variety of FireEye products to assist detecting and addressing sophisticated threats, Endpoint Security includes Universal Access Control protections, host remediation, process tracking and real-time IoC capabilities, among others. Compatible with Windows, Macs and Linux, the FireEye agent minimizes configuration requirements and responds automatically to report, contain and remediate threats.
Larger firms can leverage FireEye’s XDR platform using the firm’s Helix Enterprise platform. Designed for enterprise-scale protection, the Security-as-a-Service offering detects advanced threats, minimizes incident impact and assists centralizing security data and network protection, while also supporting compliance initiatives by helping store data for long periods.
While actual Endpoint Protection pricing is provided by FireEye, anecdotal internet data suggests pricing is in the range of about $30 per user per year. Helix Enterprise pricing is different due to scale and the number of options available and is best researched working directly with FireEye.
Fortinet Endpoint and Remote User Protection
Targeting SMBs, Fortinet Endpoint and Remote User Protection integrates endpoint detection and response with patching and vulnerability scanning, VPN protection and multifactor authentication defense to protect users, networks and data, including for on-premises systems and cloud-based software. The firm’s FortiClient software automatically scans, remotely deploys updates and protects against unpatched risks.
The enterprise-grade ML endpoint protection engine’s defenses are bolstered by additional Fortinet capabilities, including exploit prevention, web filters, automatic quarantining and patching actions and sandboxing features. Part of the broader Fortinet Security Fabric cyberdefense lineup, the Fortinet Endpoint solution also includes FortiSandbox features, both on-premises and as a platform-as-a-service option.
Compatible with Windows, Macs and Linux and Amazon and Microsoft Azure public cloud applications, Fortinet Endpoint and Remote User Protection can be licensed and deployed in multiple ways and with multiple options, all of which impact pricing. The offering is available from a variety of vendors and partners.
Microsoft Defender for Office 365
Designed to protect against a variety of advanced threats, including business email compromise, credential phishing and other common forms of sophisticated attacks, Microsoft Defender for Office 365 as an add-on service is a natural extension for organizations of all sizes using Microsoft 365 services. With AI-powered risk detection and remediation, integrated administration within Office 365 services and a security approach that includes prevention, detection, investigation, remediation and even awareness education and training, as demonstrated within Figure C, the advanced threat management platform provides additional protections for guarding email, users, systems and data.
Figure C
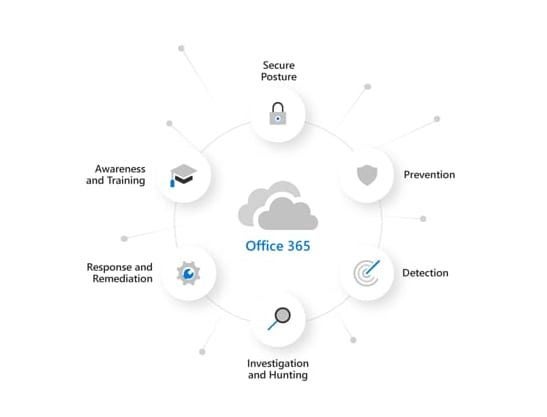
Providing advanced protection, automated response and simple configuration, Microsoft Defender for Office 365 includes built-in phishing controls, comprehensive reporting capabilities and enhanced safeguards, such as for emailed URLs, spoof protection and enhanced compromise detection to assist accelerating remediation. Robust APIs permit creating custom reports, while native support is baked in for a variety of Microsoft solutions, including such common Office applications as Word, Excel and PowerPoint, as well as OneDrive files, SharePoint sites and Teams files and communications.
Microsoft Defender for Office 365 protections are available in multiple iterations, as shown in Figure D.
Figure D

Variations include Exchange Online Protection, Microsoft Defender for Office 365 Plan 1 (Defender for Office P1) and Microsoft Defender for Office 365 Plan 2 (Defender for Office P2), while enterprise coverage is available within the form of Microsoft 365 E3, Microsoft 365 E5 and Microsoft 365 F3 plans. While numerous factors (including which Microsoft 365 plan is in place, how many users an organization has and whether subscriptions are paid monthly or annual) impact pricing, the additional Microsoft Defender expense can prove as little as just $3 per user per month.
Organizations can purchase Microsoft 365 services, including Microsoft Defender for Office 365, directly from Microsoft, from numerous online vendors or via Microsoft’s vast partner network.
RSA NetWitness
RSA, a provider dedicated to assisting organizations with managing digital risks and cybersecurity, includes an advanced threat protection solution NetWitness within its cyberdefense stable. With endpoint protection, user and entity behavior analytics (UEBA) that track user behavioral patterns, assisted incident response options and log management features, among other capabilities, NetWitness melds multiple strategies and tools within a single extended detection and response solution.
Compatible with a variety of platforms, including Amazon Web Services and Microsoft Azure implementations, NetWitness can run on appliances, hardware provided by the customer, within virtual environments and in the cloud. In addition to such common advanced threat protection features as AI- and ML-powered threat detection and response, comprehensive logging and reporting and a centralized administration and management portal, NetWitness also extends thorough forensics investigation tools.
The solution’s pricing depends upon multiple factors, including configuration model, options and the amount of information the platform processes each month.
Sophos Intercept X
Sophos Intercept X Endpoint is Sophos’ AI- and ML-powered advanced threat protection solution. With available cross-product data sourcing, ransomware file protection with automatic file recovery, behavioral analysis features, automatic detection and mitigation and a centralized management console, as highlighted in Figure E, the extended detection and response solution offers a complete ATP package for businesses of all sizes and complexities.
Figure E

Compatible with Windows, Mac and Linux operating systems, Intercept X comes in four flavors: Advanced, Advanced with XDR, Advanced with MTR Standard and Advanced with MTR Advanced.
The base implementation offers deep learning malware detection, behavioral analysis, potentially unwanted application blocking and intrusion prevention. Other features include data loss prevention and exploit prevention, active mitigation and ransomware safeguards.
Moving up to Intercept X Advanced with XDR adds additional detection protections. Examples are SQL querying protections and cross-product querying.
Intercept X Advanced with MTR Standard and Advanced add human-led threat hunting and response features. Examples include threat neutralization and remediation support and direct call-in support, respectively.
A complete product and feature breakdown is available on Sophos’ site. Pricing is per-user and varies by version but starts as low as $20 per user per year. The company’s business-grade licenses and services are sold via resellers and MSPs.
Trend Micro Vision One
As is common among advanced threat protection providers, Trend Micro collects a range of ATP products and services within a branded lineup. In Trend Micro’s case, its Vision One XDR offering is purpose-built to provide in-depth and widespread protection, as highlighted in Figure F, against a variety of advanced and sophisticated threats and vulnerabilities.
Figure F
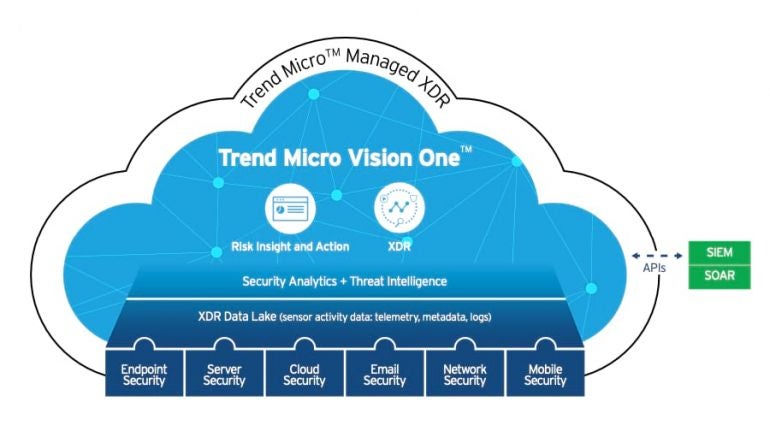
Traditional cybersecurity strategies often required collecting security reporting and incident information from multiple cyberdefense platforms deployed separately for email, computers, devices, network equipment, servers and cloud platforms. Such data then needed to be organized, reviewed and understood to identify patterns, determine status and plan an effective response. Vision One, with AI- and ML-powered capabilities, automatically collects and correlates vulnerability, cybersecurity and status information across an organization and assists preventing attacks thanks to automated reactions.
An intuitive console assists simplifying deployment, monitoring and management. Proactive policy management, meanwhile, assists adjusting settings and configurations to maintain optimal network operation.
Notably, network threat detection and response capabilities integrated within Vision One are just part of Trend Micro’s cyber defense approach. The firm’s Deep Family Advanced Threat Protection offerings further extend advanced security protections.
The Trend Micro family offers a variety of ATP options for organizations regardless of size. By leveraging its Deep Discovery technologies that provide AI- and ML-powered detection, analysis and response for advanced and targeted cyberattacks, and with optional custom sandboxing features and the ability to quickly apply threat intelligence collected worldwide, numerous solutions are available for addressing a variety of needs.
For example, Trend Micro solutions can also be deployed onsite. With a network appliance to power its Deep Discovery Inspector option, the offering can monitor network traffic across all ports and applications to support scaling across enterprise environments.
Another example of the firm’s solutions’ scalability is Trend Micro’s Deep Discovery Analyzer, a customizable sandbox that assists safe examination and improved response for a variety of potential malicious attacks. Deep Discovery Director is another example. The on-premises equipment assists coordinating the centralized deployment of updates, breach investigation and enterprise support. Further, Deep Discovery Analyzer as a Service and XDR for Networks components can be added, at additional cost, to provide cloud sandboxing and the ability to collect and relate network threats for better detection and response.
VMware Carbon Black Cloud Endpoint Standard
Organizations dependent upon VMware ESXi will find a natural service extension in the company’s Carbon Black Cloud Endpoint Standard offering that effectively consolidates multiple endpoint security functions within a single console. The next-generation endpoint detection and response solution protects against a wide range of cyberattacks.
Black Carbon replaces traditional antivirus solutions and helps secure client systems distributed across an organization, including mobile employees’ computers and multiple office locations. With no appliance required, the service requires less overhead and assists prevention and monitoring in part by integrating management and operation within a single administrative portal.
Compatible with Windows, macOS and Linux, Carbon Black protects against both known and emerging attacks, including living-off-the-land attacks in which hackers attempt to use existing legitimate processes and software to infect and compromise a system. The advanced threat protection pricing is ultimately determined by VMware’s partners, with discounts typically offered for multiple-year subscriptions. One site reports pricing per endpoint can vary from $52.99 for one year to $38.40 for a five-year commitment.








